Introducion - Secure configuration
A secure configuration is a set of settings that minimises the risk of incidents with the software you use. It is also important to make improvements where possible to enhance the level of security compared to the default configuration received “out of the box”.
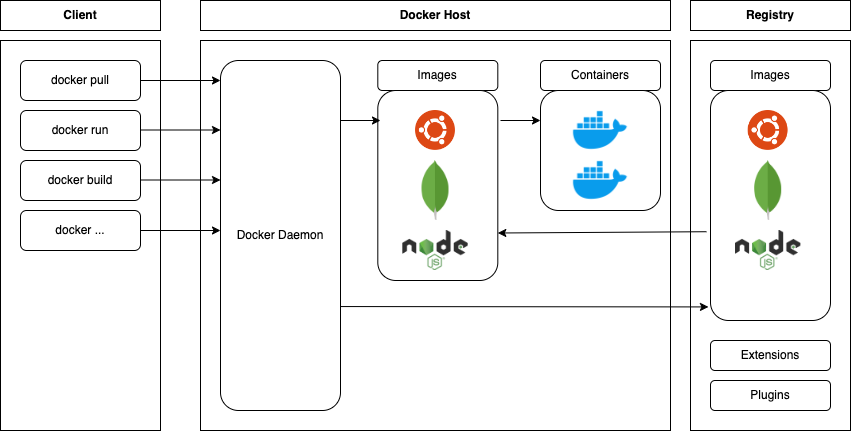
Figure 1. Docker platform architecture (own work based on https://docs.docker.com/get-started/overview/)
In the context of Docker, we will focus on securing key elements of the platform, as shown in Figure 1:
- Docker Host – this is the machine (system) on which Docker runs containers. The security of containers is closely related to the level of security of the Docker Host. It is recommended that this machine does not perform any additional roles, which helps to minimize the attack surface. It is also beneficial to use images of operating systems without unnecessary packages (so-called minimal images),
- Docker Daemon – this is a service responsible for managing Docker containers. It monitors and manages images, containers, networks, and volumes. It also facilitates communication with other Docker daemons. Typically, the Docker Daemon runs on the same machine as the Docker Host, but it is not a rule, as Docker allows them to be run on separate machines,
- Images and Containers – Docker images are templates that contain the software and configuration needed to run applications. Docker containers are running instances of images. They can be compared to virtual machines, but are lighter (they don’t contain the system layer). A container includes everything needed to run an application, ensuring compatibility across various environments and platforms.
The points presented in the further part of the article will assist in implementing improvements in the configuration, protecting against errors and vulnerabilities in the mentioned areas.
Before you start implementing security hardening recommendations, remember to test their performance in a testing environment. It is not recommended to make any changes in production environments without prior verification!
Keep in mind that not all recommendations will be suitable for your specific case. Do not treat the list below as a set of instructions that must be fully implemented. Although generally, the more of these recommendations are implemented, the better, it is not a requirement.
Exercices
Sign in to attempt the exercises in this chapter.